Most modern Linux distributions come with a firewall package already active. Since it’s often set in an ‘allow-all’ mode, people are often unaware of it.
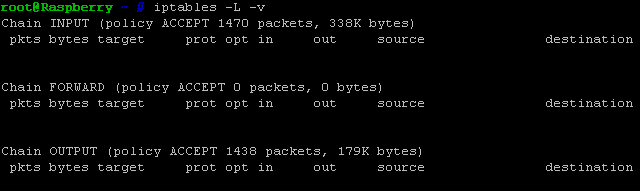
Meet iptables, a basic yet powerful stateful firewall. You can see a default ‘allow-all’ policy above. Note that there are three different chains: INPUT, FORWARD and OUTPUT. Traffic can only match one of these three chains.
- INPUT is for all traffic that is destined for the local Linux. It’s typically used to filter local services, e.g. you can allow only certain subnets to connect to the Linux via SSH, or shield off a port used by a process that you don’t want to be visible from the internet. This is also for response traffic from connections initiated locally.
- FORWARD is for all traffic traversing the device. This requires routing functionality to be activated. On Debian-based Linux versions you can do this by adding or modifying the line net.ipv4.ip_forward=1 in /etc/sysctl.conf and perhaps adding some static routes.
- OUTPUT is all traffic that originates from the local Linux. This is both for outbound connections as for response traffic for local services.
Looking at the current rule set can be done with iptables -L -v, where the optional -v parameter displays extra detail. Adding a rule can be done with iptables -A followed by the chain and the parameters of the rule. The most common ones are:
- -p defines the protocol: udp, tcp, icmp or an IP Protocol number. You can modify the /etc/protocols file to make Linux recognize an IP Protocol number by name.
- -i is the incoming interface. This is not supported in the OUTPUT chain for obvious reasons.
- -o is the outgoing interface. This is not supported in the INPUT chain.
- -s is the source subnet or host.
- -d is the destination subnet or host.
- – -dport (without the space) is the destination port, only valid if the protocol is defined as TCP or UDP. This can be a single port or a range, separated by a double colon.
- – -sport (without the space) is the source port, or range of ports.
- -j is the action to take. For the purposes of this article, let’s assume only ACCEPT and DROP are possible. More options will be discussed in upcoming blog posts.
The parameters not defined in a rule are assumed to have the value ‘any’. Examples:
- Add a rule to allow SSH to the local Linux from one single host 192.168.5.5:
iptables -A INPUT -p tcp -s 192.168.5.5 –dport 22 -j ACCEPT - Allowing subnet 10.0.1.0/24 to do Remote Desktop to server 10.100.0.10:
iptables -A FORWARD -p tcp -s 10.0.1.0/24 -dport 3389 -j ACCEPT - Block any traffic through the device towards UDP ports 10000 to 11000, regardless of source and destination:
iptables -A FORWARD -p udp –dport 10000:11000 -j DROP - Don’t allow any traffic from interface eth4 to interface eth6:
iptables -A FORWARD -i eth4 -o eth6 -j DROP
There is one additional rule which you will likely need in the configuration, but which differs from the rest of the rules: the stateful traffic rule. Although iptables by default keeps a state tables, it does not use it for traffic matching unless you tell it to. The rules to do this:
iptables -A INPUT -m conntrack –ctstate ESTABLISHED -j ACCEPT
iptables -A FORWARD -m conntrack –ctstate ESTABLISHED -j ACCEPT
iptables -A OUTPUT -m conntrack –ctstate ESTABLISHED -j ACCEPT
This calls in the module for connection tracking (-m conntrack) and matches any connections which have been seen before (ESTABLISHED). It is best to add this rule first this to avoid any drop rules from dropping traffic from known connections.
To modify the default policy, use the -P switch. For example, to block all local incoming connections by default:
iptables -P INPUT DROP
WARNING: When configuring iptables for the first time, especially via SSH, you have to be careful not to lock yourself out of the system. On top of that, some processes use IP communication using the 127.0.0.1 loopback IP address internally. If you tell iptables to block this, it may break some applications!
Review what you want to achieve. For example, say you want to change the default iptables policy to drop any incoming connections, except http traffic and ssh from your computer:
- First add the rules allowing internal and stateful traffic:
iptables -A INPUT -m conntrack –ctstate ESTABLISHED -j ACCEPT
iptables -A INPUT -i lo -j ACCEPT - Then add the rules allowing the connections:
iptables -A INPUT -p tcp –dport 80 -j ACCEPT
iptables -A INPUT -p tcp -s 192.168.1.10 –dport 22 -j ACCEPT - Finally set the policy to deny by default:
iptables -P INPUT DROP

The OUTPUT chain can stay with a default allow action. If you modify it as well, be sure to add the rules for internal and stateful traffic again.
You can check the state table live via cat /proc/net/ip_conntrack
![]()
Here you see an example of one SSH connection and a NTP connection in the state table.
These are the iptables basics. In upcoming blog posts, I’ll talk about NAT, IPv6, optimization, hardening iptables security and increasing the scalability for large rule sets.
