Welcome back to Nightmare on VPN street with TMG and SSTP – Part 3 of 4. If you’ve been following along, we’re going to configure the TMG server to remove the old cert/listener and replace it with the new cert/listener.
If you want to go back to Part 2 or Part 1, click respectively.
Here goes:
Now that we have the certificate installed in the Computer account of the TMG server, now we have to clean up TMG first, then reconfigure TMG to use the new certificate as well as manipulate the registry.
Step 1: Delete the certificate
- Go right back to the Computer certificate store and remove the certificate. There are other ways to expire the cert, etc, and I just chose to remove it. YMMV
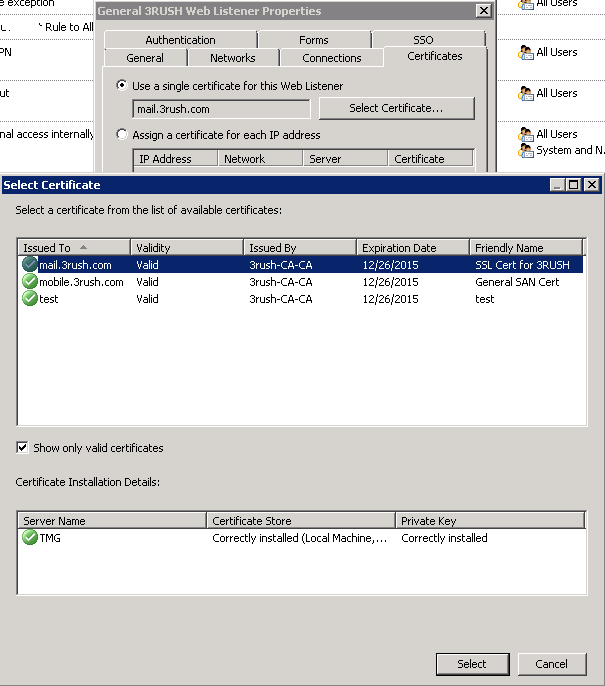
- Go to the TMG administration tool and click the Web Listeners under Network Objects
- Get the properties of the web listener and select the Certificates tab
- Under “use a single certificate for this Web Listener”, choose the Select Certificate button and choose your newly created certificate and press the Select button when done. Then you’ll need to click Apply on the TMG main page.
With that done, it’s time to move on to the HARD part. This is the area where most of my time was spent troubleshooting and researching and doing more troubleshooting.
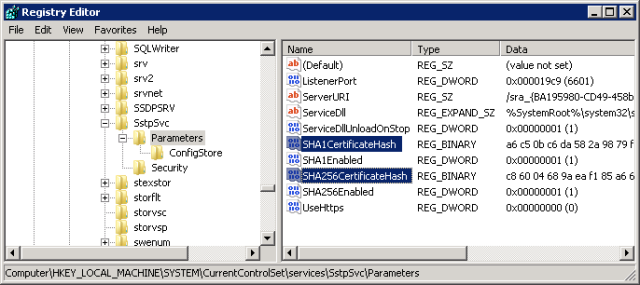
The trick here is to look in the registry and see that there are hashes in the following key:
HKLM\SYSTEM\CurrentControlSet\services\SstpSvc\Parameters
In my case, these values were here – but were the expired ones – further, TMG nor the OS doesn’t update them. This is why, although I had a new certificate, SSTP was failing. Also, deleting these keys and restarting the server will NOT register the new certificate here. This is something you would expect to work – after all, when I did the first certificate way back in 2010, I didn’t have to touch this at all. Hence the confusion and difficulty troubleshooting. Kudos to Amit Kumar’s blog post that led me in the right direction eventhough it wasn’t exact the solution to my problem.
So here was my next few steps:
- netsh http delete ssl 0.0.0.0:443netsh http delete ssl [::]:443reg delete HKLM\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA256CertificateHash /f
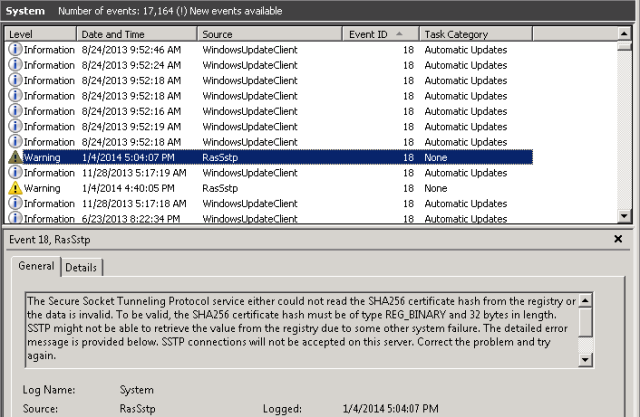
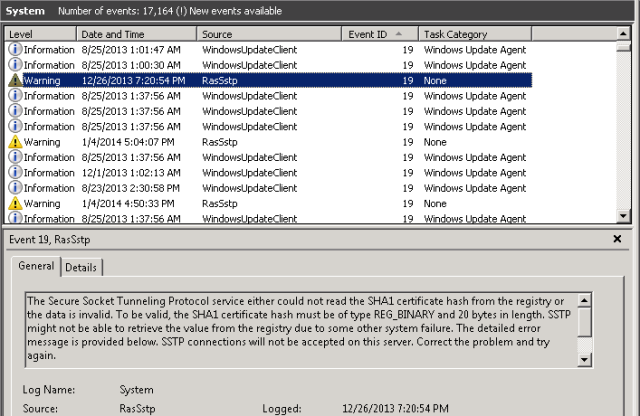
reg delete HKLM\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA1CertificateHash /f - Reboot the server – you will get some errors upon reboot in the eventlog about Event ID 18 and 19 and not being able to find SHA256 and SHA1 certificates, etc. That’s ok. This is basically telling you those two reg entries above are missing or are wrong. Here’s the error:
- Next, doing the following command will show if there are bindings or not.
netsh http show ssl
If there are bindings, then make sure they’re the new cert. If there are no bindings, good.
 (or they’re the old cert bindings, delete them again.)
(or they’re the old cert bindings, delete them again.) - Now we need to add the SHA1 bindings (you did copy them from the certificate you created in Part2, right? :>) – you cannot add the SHA256 bindings (YET) because we don’t know the hash for SHA256 (see later in part 4).
- Here’s what that commands look like
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA1CertificateHash /t REG_BINARY /d 50fd47d6fa1436c047e6a7b388b5fc2e9efd6c49 /f - Also, while were here, we need to add a DUMMY SHA256 hash (remember we don’t know the real hash yet). Here’s the actual dummy hash I added – note the SHA256 is longer than SHA1 (making it stronger):
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA256CertificateHash /t REG_BINARY /d d075f96f979fd4df20f3fdf7a5335807879ca627e5f3fc0bab7a7ac067c831c6 /f - Now, we need to make sure we BIND the SHA1 hash to the TMG nic(s) both to the IPv4 interface and the IPv6 interface. Keep in mind that the appid is the same for all RRAS SSTP implementations (it would appear according to Amit Kumar):
netsh http add sslcert ipport=[::]:443 certhash=50fd47d6fa1436c047e6a7b388b5fc2e9efd6c49 appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MYnetsh http add sslcert ipport=0.0.0.0:443 certhash=50fd47d6fa1436c047e6a7b388b5fc2e9efd6c49 appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY - Now at this point, we need to restart basically everything – I just rebooted my TMG server. However, it appears you might be able to just restart the SSTP Service which will, in turn, restart 6 or other services related to this event. A reboot felt cleaner to me :>)
Now we’re off to Part 4. You can click here to get there. In Part 4, we’ll use a client to try to connect to the TMG server using SSTP – it should connect, then disconnect. [There are a bunch of google entries out there but none really address the underlying problem – a bogus or missing SHA256 entry – we’ll address this next].